Cybercriminals find small and mid-size company vulnerabilities
There’s a very good chance that right now, at this moment, your company’s cybersecurity defenses are being tested – or attacked – by cybercriminals. By the time you finish reading this article, a hacker has most likely attempted to identify your network vulnerabilities and possibly even exploited them.
The COVID-19 pandemic increased cybercrimes exponentially. Many businesses failed to put proactive measures in place enabling criminals to gain unauthorized access to their network without much effort. Today, companies are more exposed than ever to malicious acts, theft, and loss of reputation.
SMBs are more likely to be targeted in cyberattacks
Small and medium-sized businesses (SMBs) are particularly easy targets as they lack the ability to defend themselves from knowledgeable criminals who prey on their inadequate resources and preparedness. In fact, more than four of every ten cyber-attacks target small businesses and while forty-three percent of cyberattacks are aimed at small businesses, only 14% are prepared to defend themselves, according to Accenture.
After the event, SMBs struggle because the costs of recovery and business continuity are staggering – lost revenues, downtime, financial restoration, remediation, damaged brand and reputation, the list goes on. Fewer than 10% have cyber liability insurance to support a partial or complete return to business. The National Cybersecurity Alliance reports that about 10% of small businesses go out of business in the months that follow a cyberattack and 60% are out of business within six months.
According to a Small Business Association (SBA) survey, 88% of small business owners felt their business was vulnerable to a cyberattack. Yet the majority can’t afford professional IT solutions, don’t have time to devote to cybersecurity, or simply don’t know where to begin.
We know a thing or two about assessing business risk. At Freed Maxick, we have a team of cybersecurity specialists working with SMBs to custom-create safeguards that protect their brand.
Cyberattack Prevention: First steps, first
Hackers typically do reconnaissance to find points of entry for their attack, such as file permissions, running network services, operating system platforms deployed, trust relationships, and user account information. We do the same as part of network “footprinting”. This information then is used to create our plan of attack.
There are many types of footprinting techniques deployed in discovery that are generally used for information gathering. The footprinting of external systems is one of the techniques to help to determine the amount of information available through public sources concerning your organization.
To better understand this process, try putting yourself in the hacker’s shoes and determine, through your own investigation: Where are your business’ vulnerabilities? How might hackers exploit them? What do you need to do to close or shut down those opportunities? Is there any information publicly available, like email addresses or names of key officers and internal resources, that might be used as part of a social engineering attack?
The footprinting process can include, but is not limited to:
- Online telephone directory searches
- Website(s) reviewed for information-gathering potential
- Mapping of domain names used
- Mapping of domains linked to your domain names used
- Web searches performed to discover any private or sensitive information available through public sources
- American Registry of Internet Number searches
- Domain Name Service lookups
- Traceroutes of public systems
- Email harvesting
Once gathered, an attacker will then determine the value of the information obtained through the footprinting process that could further his/her/their efforts to compromise your network. These become the steppingstone for a possible attack plan.
Executing cyberattack prevention and cybersecurity protection
We begin with vulnerability scans. This automated assessment reviews the organization’s information system to identify, evaluate, and assign severity levels of susceptible areas in order to best mitigate them. We then utilize manual Penetration Testing, a form of ethical hacking that seeks to pierce a company’s cyber defenses to find exploitable vulnerabilities in networks, web apps, systems, and user security. You can learn more about the penetration testing services and approach that we offer here.
Penetration testing that is done by credible experts like ours, is always built upon frameworks and best practices from industry-recognized organizations such as the National Institute of Standards and Technology (NIST), the Center for Internet Security (CIS), the PCI Security Standards Council (PCI SSC), the Payment Card Industry’s Data Security Standard (PCI DSS), and the SANS Institute (officially the Escal Institute of Advanced Technologies, Inc.).
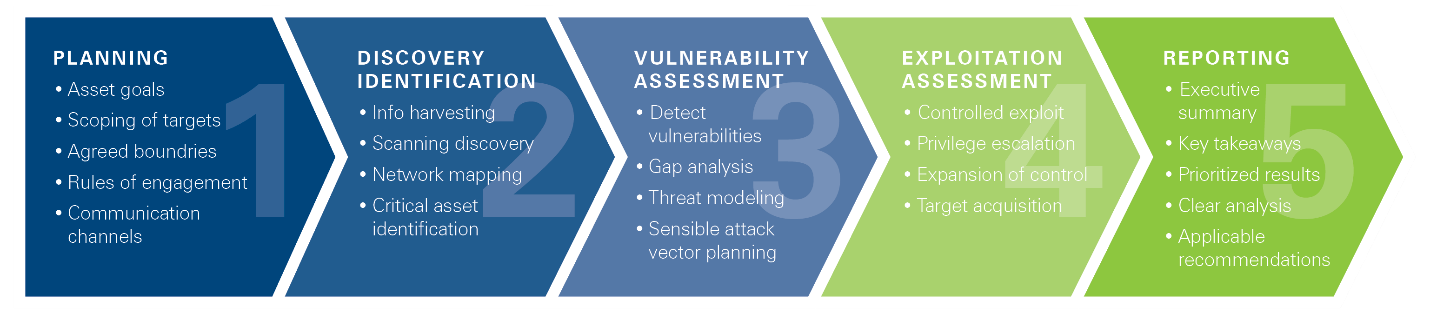
Key objectives include:
- Identify exploitable issues so that effective security controls can be implemented
- Test the robustness of security systems and policies
- Assess regulatory compliance status
- Check the employees' security awareness
- Evaluate the organization’s ability to identify and respond to security issues and incidents (e.g. is the Security Incident and Event Management System working to identify our attack)
The costs of doing business today must include a budget for a robust cybersecurity defense and cyber-liability insurance. Some industry experts say an SMBs cybersecurity budget should be at least 3% of a company’s total spending. Partnering with a reputable, knowledgeable team of professionals can provide the trusted guidance necessary to improve your security and peace of mind.
How at risk of a cyberattack do you believe your organization to be?
Contact David Hansen, Director of Risk Advisory Services, for a complimentary 30-minute cyber consultation. He can be reached directly at 585-360-1481 or David.Hansen@FreedMaxick.com
The Freed Maxick Cybersecurity team provides cybersecurity guidance and resources for small and mid-sized businesses. Click here to download our complimentary Freed Maxick Assessment Tool.


